For years, small and mid-sized businesses (SMBs) relied on firewalls, antivirus and VPNs to keep attackers out. But in 2025, with hybrid workforces, cloud apps, and increasingly sophisticated cyber threats, those perimeter defences are no longer enough. Zero Trust security; once reserved for large enterprises, is now becoming essential for SMBs too.
According to the UK’s National Cyber Security Centre (NCSC), small organisations are frequently targeted by ransomware, phishing and credential-theft attacks because they are seen as “soft targets”. Zero Trust flips the traditional “trust but verify” model on its head, enforcing “never trust, always verify” for every user and device, whether inside or outside your network.
What Is Zero Trust Security in Simple Terms?
At its core, Zero Trust is not a single product but a security framework. It assumes that no user, device or application should be trusted by default, even if they’re inside your corporate network.
Key principles include:
- Verify explicitly: Always authenticate and authorise based on all available data points (identity, location, device health, data classification).
- Use least privilege: Give users only the access they need and nothing more.
- Assume breach: Design your systems as if attackers are already inside, so you can contain and detect them quickly.
This approach protects SMBs against stolen passwords, compromised devices, and lateral movement inside the network, threats that traditional VPNs and firewalls struggle to stop.

Why Zero Trust Matters for UK SMBs
Small businesses now face the same threats as big enterprises but with fewer resources. Some stats:
- The UK Government’s Cyber Security Breaches Survey 2024 found that 59% of medium-sized businesses and 54% of small businesses reported a cyber incident in the past year (GOV.UK).
- Average cost of a cyber breach for UK SMBs: £15,300 per incident (same source).
- New EU and UK regulations (like NIS2 and Cyber Essentials Plus) are tightening requirements for access controls and monitoring.
Zero Trust helps SMBs:
- Reduce breach risk: Every access request is verified, limiting attacker movement.
- Secure hybrid work: Employees, contractors, and partners can safely access apps from anywhere without a “flat” VPN tunnel.
- Align with compliance: Principles such as strong authentication, device checks, and segmentation map directly to Cyber Essentials and NIS2 obligations.
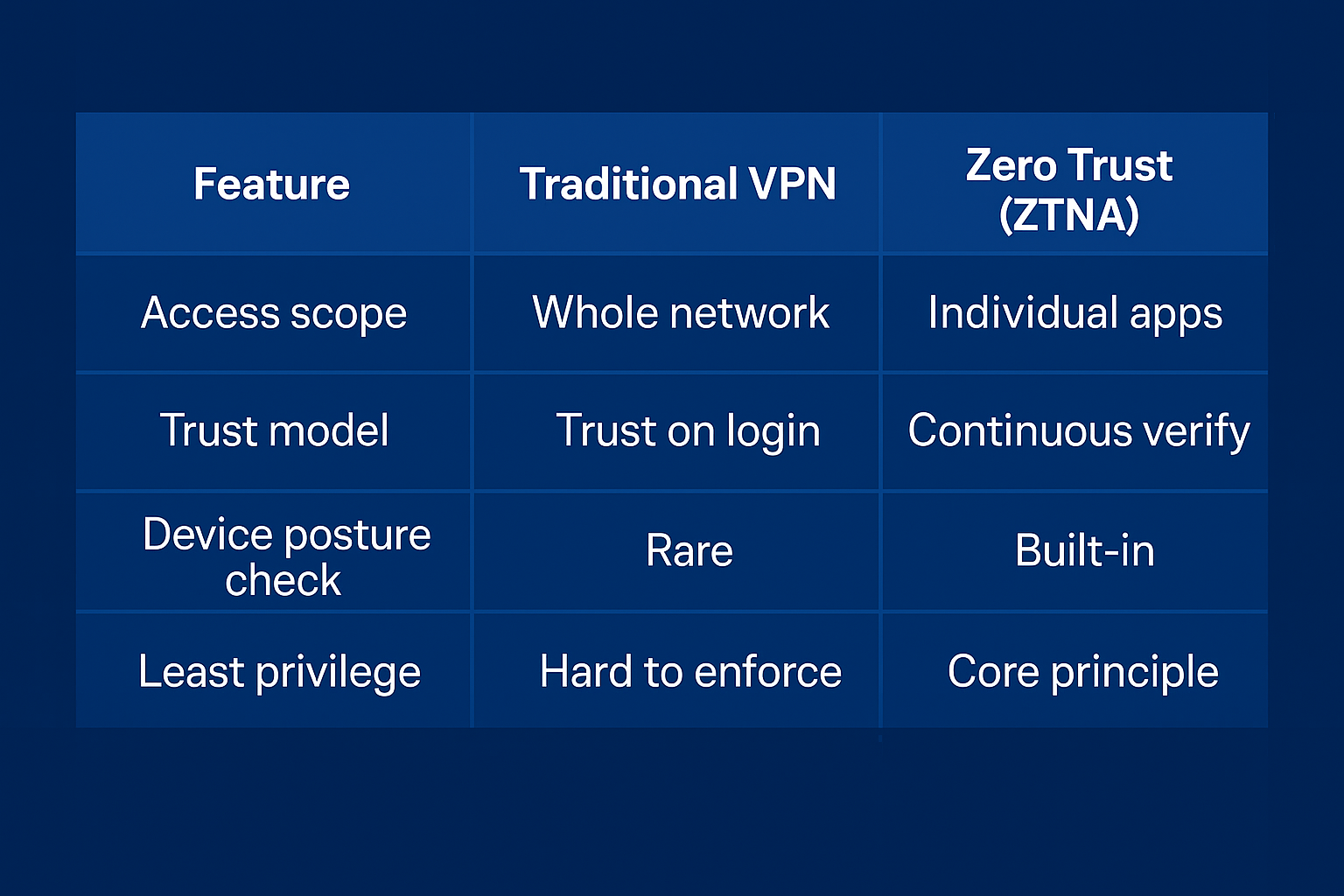
Zero Trust vs. VPN for Small Businesses
Many SMBs still rely on VPNs to secure remote access. While VPNs encrypt traffic, they typically grant broad, network-level access once connected. If a user’s credentials are stolen, an attacker can roam freely.
Zero Trust Network Access (ZTNA), on the other hand, grants application-level access only after verifying user identity, device posture, and context each time. This dramatically reduces lateral movement.
A 5-Step Zero Trust Checklist for SMBs
You don’t need an enterprise-size budget to start. Here’s a practical roadmap for implementing Zero Trust in a small business:
1. Enable Multi-Factor Authentication (MFA)
Make MFA mandatory for email, VPN, and cloud apps. It’s the fastest, cheapest way to block credential attacks.
2. Adopt Single Sign-On (SSO) and Identity Management
Centralise authentication with a reputable identity provider. This simplifies access control and audit trails.
3. Segment Access by Role (Least Privilege)
Limit each user’s access to only the apps and data they need. Use role-based access and network segmentation.
4. Check Device Posture
Ensure devices meet security baselines (patched OS, antivirus, encryption) before granting access.
5. Monitor and Improve Continuously
Feed logs into your SIEM or managed detection service. Track anomalies and refine policies over time.
These steps align closely with guidance from the UK NCSC and CISA Zero Trust Maturity Model.
Tools That Make Zero Trust Practical for SMBs
You don’t have to build Zero Trust from scratch. Many affordable solutions now package core capabilities:
- Identity & Access: Microsoft Entra ID, Okta, JumpCloud.
- ZTNA Gateways: Cloudflare Access, Zscaler, Netskope.
- Endpoint Security: Microsoft Defender for Business, SentinelOne, CrowdStrike.
- Monitoring: Managed SIEM/XDR providers or in-house tools.
Your implementation may start with identity (MFA/SSO) and device posture, then expand to ZTNA and continuous monitoring as budget allows.
Common Pitfalls (and How to Avoid Them)
- Over-provisioning access: Don’t copy your old flat VPN model into Zero Trust.
- Skipping device checks: Verifying identity without checking the device leaves a hole.
- Big-bang rollout: Start small, prove value, then scale.
- Neglecting monitoring: Without logs and alerts, Zero Trust loses its power.
Final Thoughts
For UK SMBs, Zero Trust security is no longer optional. It’s the modern way to protect against ransomware, insider threats, and compliance headaches without slowing your team down. Starting small, with MFA, SSO and role-based access, can dramatically reduce your risk.
At I-NET Software Solutions, we help SMBs design and implement Zero Trust strategies tailored to their size and budget, integrating MFA, SSO, device posture and monitoring into a seamless whole.
Book a Zero Trust readiness assessment today to see how we can secure your business without adding complexity.
Zero Trust helps SMBs strengthen access and data security, but full protection also means staying compliant with UK and EU regulations. See our post Cybersecurity Compliance 101: A Guide for SMBs in the UK and EU.
