Hybrid and remote work are now business‑as‑usual. Recent UK data shows that 28% of working adults were engaged in hybrid working early in 2025. Yet cyber‑attacks targeting remote‑enabled organisations are rising, average costs exceed £10,000 per incident.
For small and medium‑sized businesses (SMBs), remote work introduces new exposure: unmanaged devices, insecure home networks, and limited oversight. To stay resilient, adopting remote work cybersecurity best practices is no longer optional, it’s a business imperative.
Why Remote Work Cyber Risks Matter for SMBs
A UK survey of 500 SME owners found 23% identified remote working as a major cybersecurity concern and 69% admitted they lacked a cyber‑security policy.
Bring‑Your‑Own‑Device (BYOD) practices compound the risk: One UK study found 61% of SMEs experienced an incident after introducing BYOD.
Combine these statistics with the fact that many hybrid teams operate outside the traditional corporate perimeter, and it’s clear: remote work isn’t just a shift in where people work, it’s a shift in how you must protect your business.

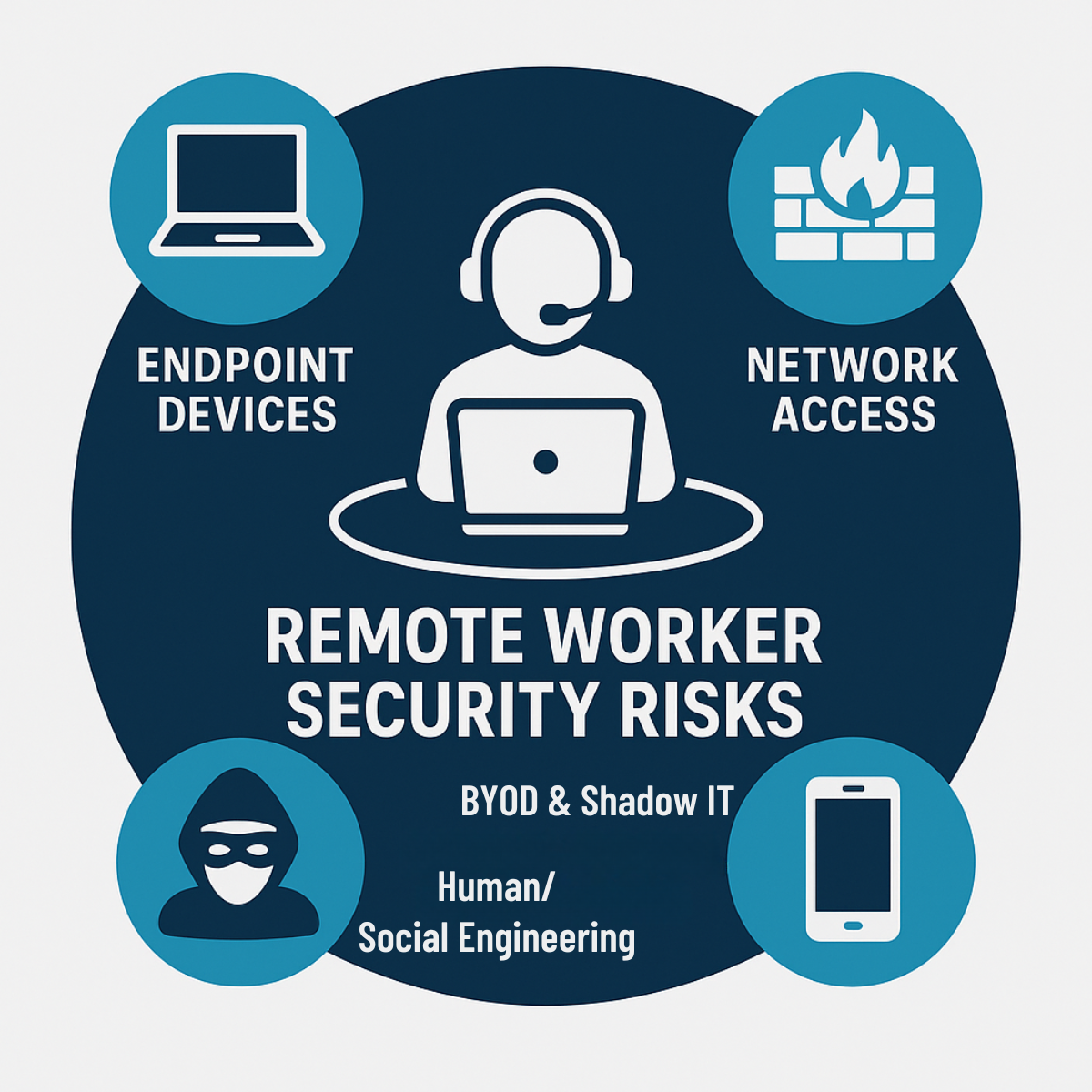
Four Key Risk Areas for Remote/Hybrid Teams
Here’s a practical framework to highlight where most remote work cyber risks emerge:
a) Device & Endpoint Control
Endpoints become the new perimeter. Home‑based laptops, personal smartphones or tablets may be used for work without sufficient oversight. The “mobile threat” report for UK SMEs found 42% of organisations reported a mobile or web‑app vulnerability led to an incident.
What to address: enforce device encryption, remote wipe, endpoint monitoring, and restrict privileged access.
b) Network & Access Security
Remote access often uses home broadband or public Wi‑Fi, which increases exposure. Some teams still rely solely on a corporate VPN, a model that is increasingly outdated. A recent study found only 52% of SMEs used VPNs, and just 46% had access‑control policies for remote work.
What to address: introduce Zero‑Trust Network Access (ZTNA) or software‑defined perimeter (SDP) models, enforce MFA, reduce blast‑radius.
c) BYOD & Shadow IT
Employees using personal devices and unsanctioned apps create untracked access points. A UK report showed nearly 44% of employees used their personal phone for work, even in organisations that forbid BYOD.
What to address: develop a clear BYOD policy, monitor device usage, educate staff on risks, apply mobile‑device management (MDM) tools.
d) Human Behaviour & Social Engineering
Remote work means fewer in‑person cues and more digital grooming for attacks. Phishing and credential compromise remain the most exploited vectors. The UK government’s Cyber Security Breaches Survey found that only 17% of UK organisations carried out staff training in 2022.
What to address: deploy “remote‑work”‑specific training, simulate phishing for remote users, reinforce reporting procedures.
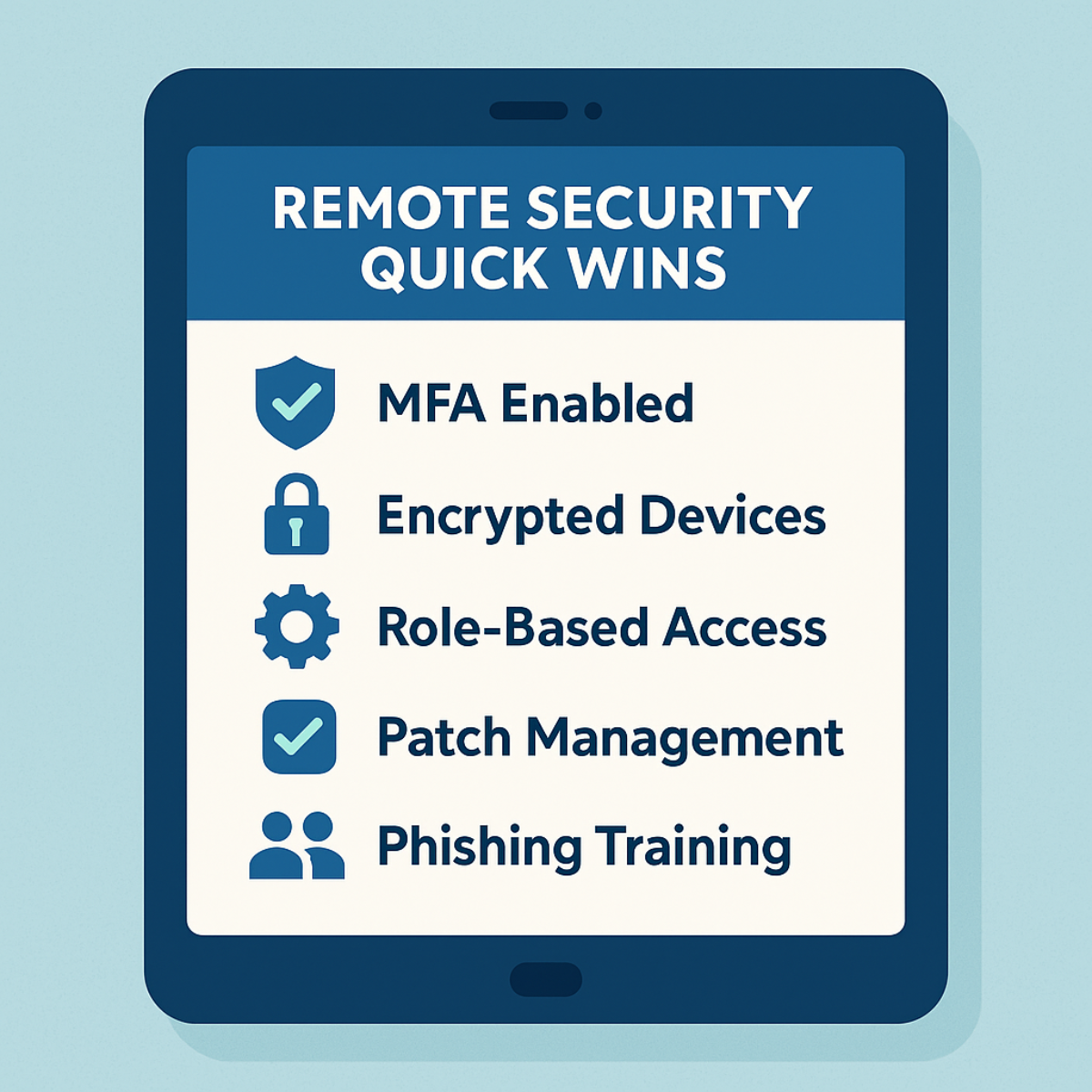
Quick Wins for Remote Work Security (No Full Overhaul Required)
You don’t need to rebuild your entire infrastructure. Here are targeted, cost‑effective fixes you can implement this quarter:
- Enforce MFA everywhere. The evidence is clear that MFA significantly reduces account compromise.
- Enable remote‑wipe and encryption. Devices outside the company office must protect corporate data if lost or stolen, 40% of breaches in BYOD incidents involve lost devices.
- Segment access by role. Not every employee needs full network access. Use least‑privilege principles with remote roles.
- Replace VPN with cloud‑native access. Modern hybrid teams benefit from ZTNA over traditional VPNs, lowering risk of lateral movement.
- Update and patch regularly. While remote, devices might not auto‑update, enforce patching through policy.
- Deliver remote‑specific security awareness. Training should focus on home‑office threats: unsecured routers, mobile taps, video‑call hijack.
Measurement & Metrics: Tracking Remote Security Success
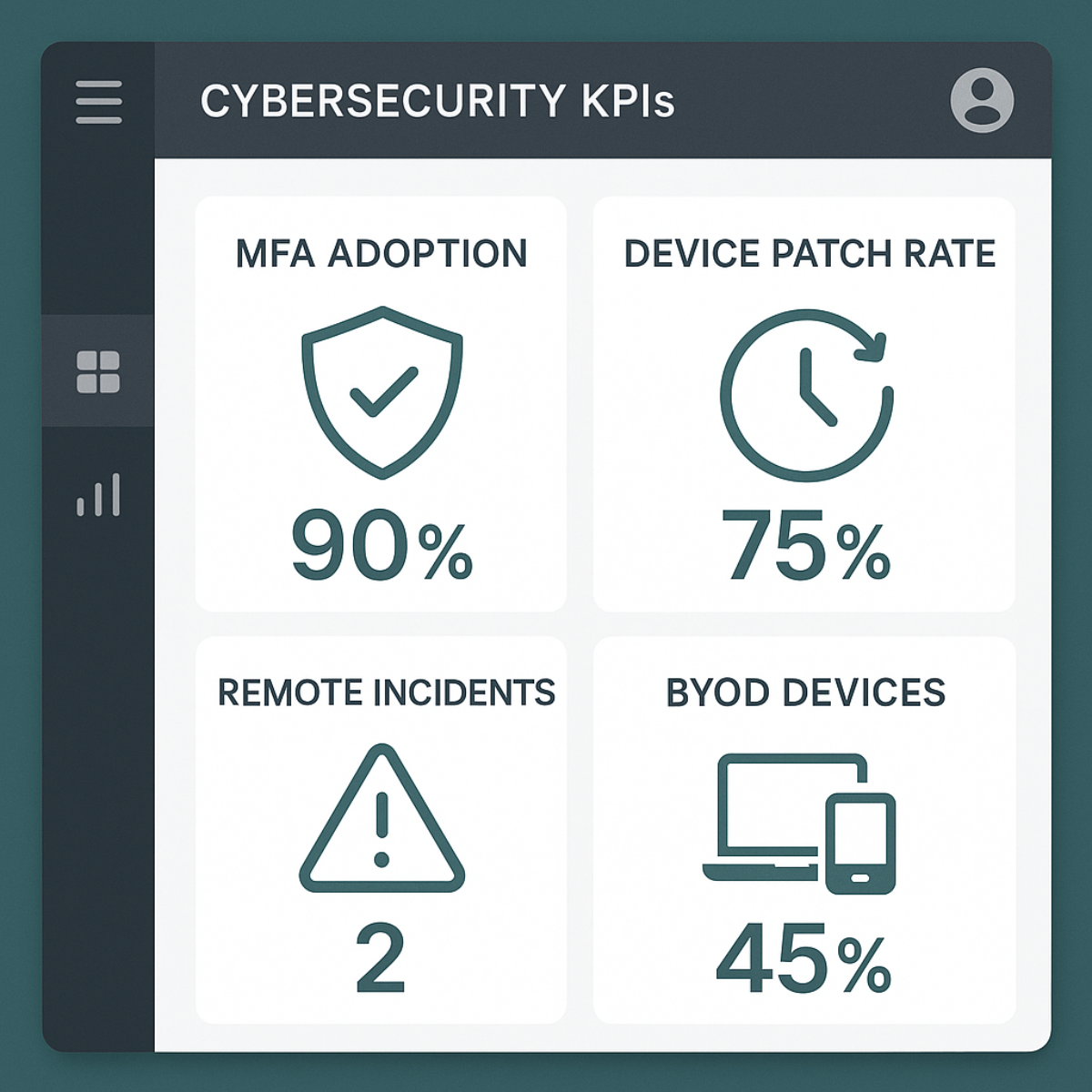
To prove ROI and monitor progress, track these key indicators:
- Percentage of remote devices under MDM control
- Multi‑factor authentication adoption rate
- Time to patch remote endpoints (average days)
- Number of remote‑work‑related incidents
- Distance (days) from last phishing click among remote staff
A strong measurement regime helps justify investment and drives sustained improvement across remote workflows.
Conclusion
Remote work isn’t going away. For UK SMEs, the ability to adapt securely has become a competitive advantage. With 23% of SMEs identifying remote‑work as a major cyber concern and nearly £10k+ average cost per hybrid‑work attack, the stakes are high.
However, you don’t need a large IT budget or a full re‑build to increase security. A focused strategy around device control, access, BYOD oversight and human training can significantly reduce risk.
Ready to get started? Book a free 15‑minute Remote Work Cyber Risk Review with the I‑NET security team today.
Further Reading
Building a Cybersecurity Culture: What It Looks Like in Small Team
